Overview
In the project DRIM we research on basics, techniques and
usage scenarios for Privacy Enhancing Identity Management.
Partly based on previous work, the project has developed some
software libraries, which can be downloaded from this website.
The goal of the project is the developement of a functional
identity management prototype. The prototype will be tested and
evaluated in different usage scenarios. The following picture
shows the general architecture of an identity management scheme.
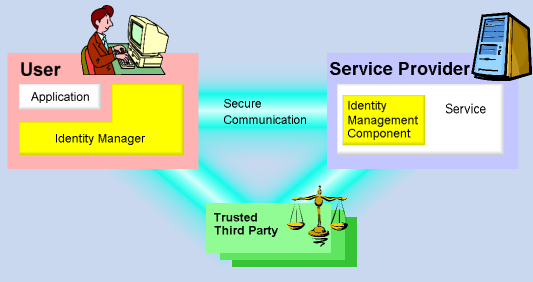
-
SSONET: A library for secure network
communication, which supports anonymous connections using the anonymity service
AN.ON.
-
IDMAN: The Identity Manager.
-
PSMAN: A library used for the management
of the identity data in a database.
-
PKI: A service, which issues pseudonyms
for users. Additionally, it can issue certificates, which state the service knows the
identity of the pseudonym holder.
-
Showcase: An example application for
identity management.
-
Web proxy: Enhancement of the web server
Jigsaw, which enables pseudonymous connections to
the web server.
What is Privacy Enhancing Identity Management?
Generally, identity management means managing the users personal data on his
own PC/PDA/Mobile Phone. The identity management concept aims at supporting the
user to act in different situations under different identities. By default,
a third party can not link such an identity to a user. So, it is more difficult
for third parties like web services or advertisement companies to
build extensive profiles about a user without user's consent.
"Management" summarizes the following actions:
-
Storing personal data in the Identity Manager.
The Identity Manager is a central place for the storage of
personal data. Applications do not need to store these data
on their own. So, a user can more easily get an overview over his
personal data stored at the PC, and applications can get access
to personal data using uniform interfaces.
-
Control over disclosure of personal data during communication.
The Identity Manager registers each item of personal data disclosed
during communication on the network. The user can see, which personal
data he gave to which communication partner. So, he is also enabled
to apply for erasure or correction of personal data by a communication
partner.
-
Specification of rules for the disclosure of personal data.
In the Identity Manager, users can configure rules, which specify,
which item of personal data shall be allowed to be disclosed to
which communication partner for which purpose. This helps preventing
unintended disclosure of personal data.
-
Usage of anonymous and pseudonymous communication links.
Identity management supports usage of (cryptographical) pseudonyms
in communication. By using different types of pseudonyms for different
actions or applications, different anonymity levels can be reached.
-
Usage of certificates and credentials for showing authentications
under pseudonym.
Attributes of a user can be linked
to cryptographical pseudonyms by certificates. Such
certificates can also be issued by third parties. By showing such a certificate,
a user can proof, that he has a certain attribute, without revealing his
full identity.
-
Support of confidentiality, integrity and anonymity on the network communication.
The Identity Manager supports confidentiality, integrity and anonymity on the network
communication. Secure communication is the basis for Privacy Enhancing Identity
Management, because it prevents from attackers eavesdropping at the network
links.
Wherefore is identity management useful?
When a user communicates on the Internet, the communication
is visible on the net, and of course to the communication
partner. Using unique identificators (e.g. IP-addresses,
Cookies, ...), transactions can easily be linked to users,
and extensive user profiles can be established. Today, users
can hardly prevent building such profiles. Surveys show that
this is a serious reason for low acceptance of Internet
services.
By incorporating pseudonyms, digital certificates and
trustee services, Privacy Enhancing Identity Mmanagement can be
a solution for the problem shown. Users act on the internet
under pseudonyms, but (authenticated) personal data can be linked
to the pseudonym by certificates. So, service providers can get
authenticated user data without neccessarily knowing
the user's real identity.
Incorporating trustee services, disclosing user identity
is possible in substantial cases.
The system suffices user's as well as service provider's needs.
 Marit Köhntopp,
Andreas Pfitzmann: Informationelle Selbstbestimmung
durch Identitätsmanagement; in: it+ti Informationstechnik und
Technische Informatik, Schwerpunktthema "IT-Sicherheit" 5/2001;
Oldenbourg Wissenschaftsverlag, München, September 2001; 227-235 Marit Köhntopp,
Andreas Pfitzmann: Informationelle Selbstbestimmung
durch Identitätsmanagement; in: it+ti Informationstechnik und
Technische Informatik, Schwerpunktthema "IT-Sicherheit" 5/2001;
Oldenbourg Wissenschaftsverlag, München, September 2001; 227-235
 Sebastian Clauß, Marit Köhntopp:
Identity Management and
Its Support of Multilateral Security; in: Computer Networks 37 (2001),
Special Issue on Electronic Business Systems;
Elsevier, North-Holland 2001; 205-219 Sebastian Clauß, Marit Köhntopp:
Identity Management and
Its Support of Multilateral Security; in: Computer Networks 37 (2001),
Special Issue on Electronic Business Systems;
Elsevier, North-Holland 2001; 205-219
Marit Hansen collected an extensive
set of
publications
about identity management.
More information about identity management can be found at the
Independent Center
for Privacy Protection Schleswig-Holstein  .
Sebastian Clauß .
Sebastian Clauß
Hans-Grundig-Straße 25
Room 115
D-01307 Dresden
Thomas Kriegelstein
Hans-Grundig-Straße 25
Room 115
D-01307 Dresden
E-Mail: sebastian.clauss@tu-dresden.de
Fax: +49 (0) 351 463-38255
|


 Marit Köhntopp,
Andreas Pfitzmann: Informationelle Selbstbestimmung
durch Identitätsmanagement; in: it+ti Informationstechnik und
Technische Informatik, Schwerpunktthema "IT-Sicherheit" 5/2001;
Oldenbourg Wissenschaftsverlag, München, September 2001; 227-235
Marit Köhntopp,
Andreas Pfitzmann: Informationelle Selbstbestimmung
durch Identitätsmanagement; in: it+ti Informationstechnik und
Technische Informatik, Schwerpunktthema "IT-Sicherheit" 5/2001;
Oldenbourg Wissenschaftsverlag, München, September 2001; 227-235 Sebastian Clauß, Marit Köhntopp:
Identity Management and
Its Support of Multilateral Security; in: Computer Networks 37 (2001),
Special Issue on Electronic Business Systems;
Elsevier, North-Holland 2001; 205-219
Sebastian Clauß, Marit Köhntopp:
Identity Management and
Its Support of Multilateral Security; in: Computer Networks 37 (2001),
Special Issue on Electronic Business Systems;
Elsevier, North-Holland 2001; 205-219 .
.